Basic IT security tips
Protection for digital doors and windows
When you get in a car, you put on your seat belt. When you leave the house, you lock the doors and windows. We barely even think about either of these things, they are just second nature to us. So why are we often so careless with our digital doors and windows and willing to run the risk of unauthorised people breaching our digital privacy?
Newsletter: Be safe every 14 days!
With the newsletter 'Sicher Informiert' (in german speech) and our Security recommendation the BSI offers informations all around IT security.
'Easy to understand' and many 'tips and tricks':
To the newsletter 'Sicher Informiert'.
As our society becomes ever-more digital, new IT applications are making their way into our everyday lives. It's conceivable that in future, lots of things will only be done online. But not everyone has the same level of experience in dealing with this ever-advancing technology. Many people find it a real challenge just to set up a smartphone securely, while others are online practically 24/7 and totally familiar with all the technologies out there. But while people's skill levels may vary widely, every one of us should be thinking about how we can use these technologies safely — ideally, before anything untoward happens.
What are the basic rules of IT security?
You don't have to be an IT security expert to take note of a few basic rules about how to use online services and Internet-enabled devices responsibly. Pay attention to your online e-mail, banking and shopping accounts, as well as your social networks. Having passwords that are sufficiently strong and complex and, where possible, authenticating your identity with a second factor are both essential here. You should never bypass these steps.
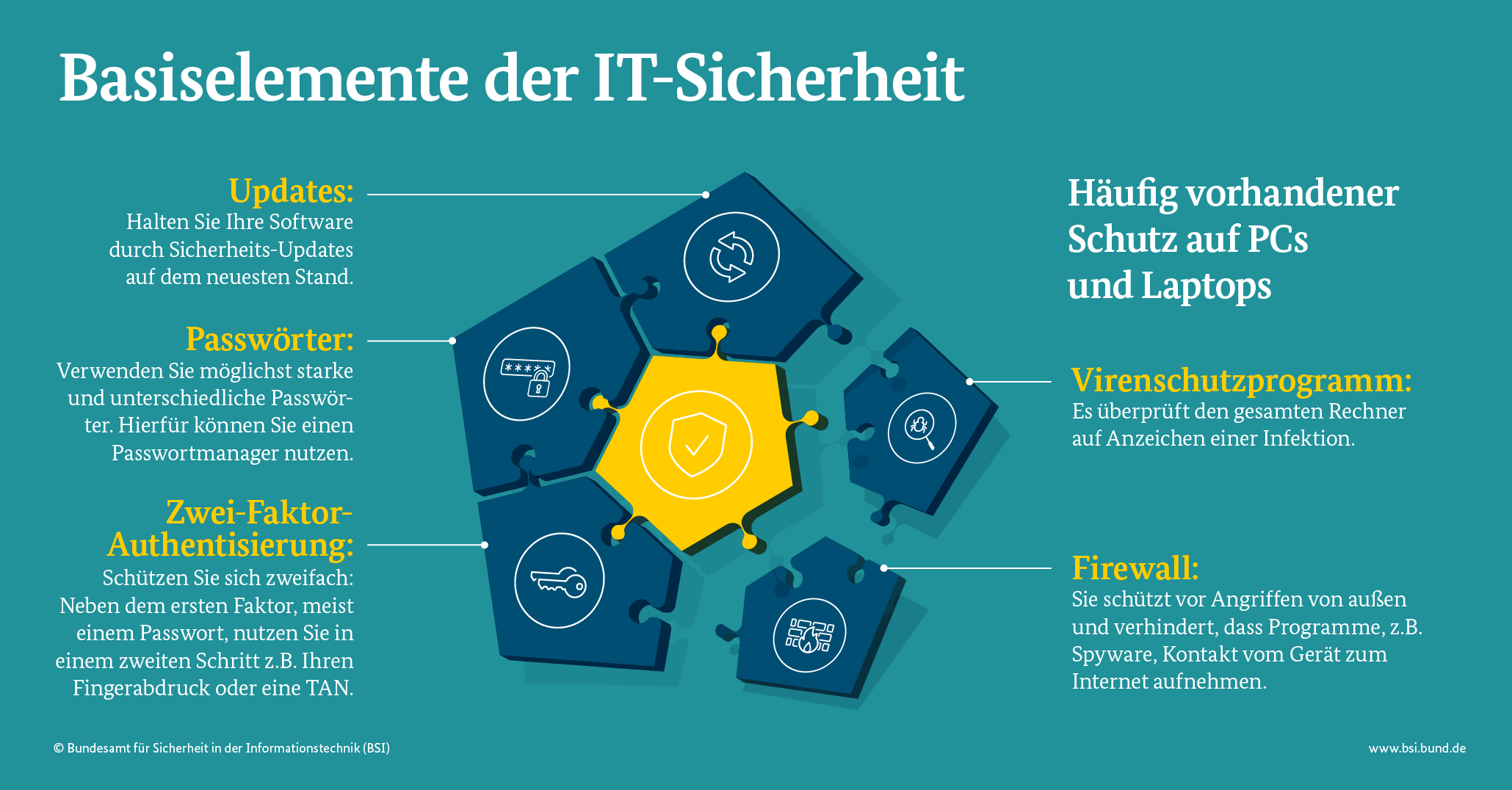
The device you use should be well protected too. The key tips here are to always have up-to-date virus protection including a firewall and to install security updates promptly (and automatically, if possible). These devices are not only your home router, laptop, smartphone or tablet. If you are thinking of purchasing or setting up other devices that connect to the Internet of Things via Bluetooth or WLAN interfaces, such as security cameras, drones, refrigerators or robot vacuum cleaners, it is also worth casting an eye over what regular updates and other security settings are available.
10 tips for using the Internet safely
Make adjustments to your web browser and keep it up to date
To surf the Internet, you will need a browser. Extensions, add-ons and plug-ins are small programs that are able to add more functions to your browser. Disable or uninstall any programs you do not really need. You can often do this under menu items of the same name in your browser's settings. This is also where you can make additional security and data protection settings to reduce the amount of confidential information that is stored and sent to third parties. 'Confidential' information is anything that discloses details about you or your online behaviour. Functions such as 'private mode' or 'clear history', for example, stop other people who use the same device from seeing which websites you have visited. 'Block third-party cookies' ensures only websites you have actually visited can track your surfing behaviour.
Make sure your web browser is always kept up to date. These updates also serve to resolve vulnerabilities.
Use an ad blocker program to protect yourself from malvertising, which is a technique that harnesses advertising to spread malware.
Carefully enter any addresses of particularly security-critical websites, such as those for online banking, into the browser's address bar manually the first time you visit. Then save that address as a bookmark, which you can use in future to access the website securely.
Keep your operating system and other software up to date
Use an up-to-date version of your operating system and the programs installed on it. Enable the automatic update function wherever possible. You can check whether your computer's operating system is up to date in the settings under 'Update'. Take note of any information about new versions of the operating system or applications.
Uninstall any programs you no longer use. The fewer applications you have installed, the fewer potential points of attack for your system as a whole.
Use virus protection applications and a firewall
All commonly used operating systems have virus protection and a firewall built in, which make it more difficult for criminals to perform attacks from the Internet even in the default configuration. Enable these functions or use a virus protection program from another provider.
Remember that this safeguard is only effective when combined with other measures and it is still important to follow the other tips contained in this brochure. Do not let an enabled virus protection program or firewall lull you into a false sense of security: they are not a cast-iron guarantee of safety.
Create different user accounts
When malware finds its way onto a computer, it obtains the same rights to the PC as the user account through which it entered. As an administrator, you have full access to almost all areas of your PC. So you should only work with administrator rights if absolutely necessary.
Set up different, password-protected user accounts for all of a PC's users. This is done via the (System) Settings, System Preferences or Control Panel, depending on which operating system you are using. Only assign the authorisations which each user actually needs to these different accounts. This is also a good way of stopping other people from accessing private files. Always surf the Internet in a restricted-access user account, not the administrator role.
Protect your online accounts and user accounts with secure passwords
Create a different, secure password for every online account and user account you have; if they could have fallen into the wrong hands, change all your passwords as soon as possible. Also change the default passwords provided by manufacturers or service providers the first time you use them.
A secure password must meet the following criteria:
- You must be able to easily remember a password.
- The longer the password, the better.
- The password should be at least eight characters long.
- You can usually use all available characters in a password, i.e. upper-case and lower-case letters, numbers and special characters.
- The full password should not be a word that appears in the dictionary. Common sequences of numbers or keyboard patterns are not suitable as a secure password either.
- It is not recommended to add single numbers or special characters to the start or end of a normal word.
If two-factor authentication (2FA) is available, you can use it to give your online account an extra layer of access protection. If you have many different passwords, a password manager can help you to handle them.
Please note: It is very important to never give your passwords to anyone else.
Further information on secure passwords.
Exercise caution around e-mails and their attachments
Wherever possible, do not display or compose e-mails in HTML format; use a plain text format instead. You can modify how you use HTML format in your e-mail program's settings. Be careful when opening e-mail attachments or clicking on links, as malware is often spread via images integrated into e-mails or files attached to them, or it is concealed behind links. You should be especially wary of this if an e-mail has been sent by someone you do not know.
If an e-mail sent by someone you do know seems a little strange, it is best to ask the sender whether the e-mail actually has come from them. However, do not use any of the options given in the e-mail to contact the sender. They could have been faked.
You can identify unwanted or dangerous e-mails by looking out for a number of things. Hover the cursor over the sender's e-mail address or click on it to see whether the sender has been faked, for example. Watch out for meaningless sequences of letters, letters being replaced by others which look similar or a foreign domain, i.e. the final part of the e-mail address. Also check the subject line and the body of the e-mail for spelling mistakes and to see whether it makes logical sense. Fraudsters often make mistakes with this. You should also be sceptical if the e-mail demands that you respond quickly.
Be careful when downloading, particularly with programs
Be careful when you download anything from the Internet, particularly if you are downloading programs. Avoid any sources that give you reason to doubt they are genuine. Make sure your source is trustworthy before you download any programs. Use search engines to find out more information about the manufacturer where applicable, or get testimonials from other users.
If possible, download the program from the manufacturer's website and use only encrypted sites, which you can recognise by the abbreviation 'https' in your browser's address bar.
Be cautious about giving out your personal data
Criminals on the Internet are more successful if they address their victims as individuals. They can use data they have previously collected without authorisation, such as your surfing habits or names of people you know, to build trust. Personal data is a form of currency online nowadays and should be treated as such. Think about which online services you really want to entrust with your personal data.
You should also avoid transmitting unprotected personal data over open, unsecured networks.
Protect your data with encryption
Only visit and enter your personal data on websites that provide an encrypted connection. If the site uses the https secure communication protocol, you can see this in its web address. The address will always start 'https' and your web browser's address bar will usually contain a small locked padlock symbol or similar. You can also encrypt confidential e-mails. Check the options offered by your e-mail provider.
If you use wireless LAN (WLAN) transmission technology to surf the Internet, pay particular attention to the encryption of the wireless network. Select the WPA3 encryption standard in your router or, if that is not yet supported, select WPA2 for the time being. Choose a complex password of at least 20 characters. You can access your router via a specific web address given in your router's manual.
If you are able to connect to your home network or its router via a virtual private network (VPN), you can access the Internet via public WLAN hotspots when you are out and about and enjoy the same high level of security you are used to at home. A VPN is an especially secure connection between two points. It creates a tunnel from a smartphone, for example, through the public Internet and to your home network, from where you can then use your own Internet connection. Modern routers frequently have an option for setting up a VPN.
Make backups at regular intervals
If one of your devices becomes infected despite all these protective measures, important data can be lost. The same applies if you lose the device itself or if it develops some other kind of fault. To minimise the resulting damage, it is important to make backups of your files on external hard drives or USB sticks at regular intervals. These storage media should be connected to your PC only when necessary. You can use cloud services to make backups of encrypted data.
Only restore your data from the backup. If you are setting up a device again from scratch, you should not take any programs from a backup, as they may already be infected.
See below for all the other recommendations that the Federal Office for Information Security (BSI) has drawn up for you regarding applications and devices. Take some time to protect your digital doors and windows.


